Tag: CyberSecurity
-

Understanding Ransomware Settlements – What You Need to Know?
Discover the consequences of paying ransoms, legal ramifications, and the comprehensive costs associated with settlements. Learn why strengthening cybersecurity measures and developing an incident response strategy is vital for businesses of all sizes.
-
Is your business data truly safe?
In this article, we will examine the current state of business data security, prevalent threats, and proactive measures that businesses can adapt to strengthen their digital defenses.
-
How to Play Poki Unblocked: Your Full Guide
Platforms like Poki.com have emerged as exciting hubs for gamers of all ages, and this comprehensive guide will offer security- and privacy-minded people a way to play Poki games safely and securely.
-

Cyber Security in the Remote Work Era: Balancing Productivity and Protection
The challenge for organizations today is to achieve a balance between productivity and protection, with the implementation of effective policies, technologies, and cyber security services being crucial in this balancing act.
-

What Is Spyware, and How Can You Protect Yourself?
Spyware can cause serious problems, such as identity theft, financial loss, and more. In this post, we will discuss the basics of spyware and explain how it works to protect yourself against it.
-
The Role of Data Destruction in Cybersecurity
Below we look at the role of data destruction in cybersecurity and why it should never be taken for granted.
-

Which Industries Use Continuous Controls Monitoring?
In recent times, one way that businesses have been lowering risk and increasing cybersecurity are through Continuous Controls Monitoring (CCM).
-

Trump administration is planning to ban end-to-end encryption
Senior Trump officials have discussed the possibility of passing new legislation that could make it illegal for companies to offer end-to-end encryption through their services.
-

Facebook is paying teens to install VPN app that collects user data
According to a recent report, Facebook is paying teenagers to install a “Research” app, which secretly tracks user activity and collects data on them.
-
Mozilla released a Firefox update to fix a critical security flaw
Mozilla has released an important update (version 58.0.1) for its Firefox web browser to patch a critical vulnerability that could allow remote attackers to execute malicious code on computers.
-

7 Best Password Managers
A password manager strengthens your security by encrypting and storing your passwords in a secured vault that is protected by a master password. We have evaluated dozens of password managers to help you choose the one that suits you best.
-

Google Introduces New Security Features To Block Unverified Apps
Today, Google is adding another layer on top of this with the launch of a new “unverified app” screen for new web applications and Apps Scripts.
-

How To Secure Your IP Camera From Hacking
IP camera can be vulnerable to hackers, due to misconfiguration, firmware, design flaws, etc. and here are few ways to secure your IP Camera from hacking.
-

10 Free Malware Removal Tools For Windows
Here, to help you accomplish the usually-tough task of removing malware from your PC, we have compiled a list of 10 best malware removal tools.
-
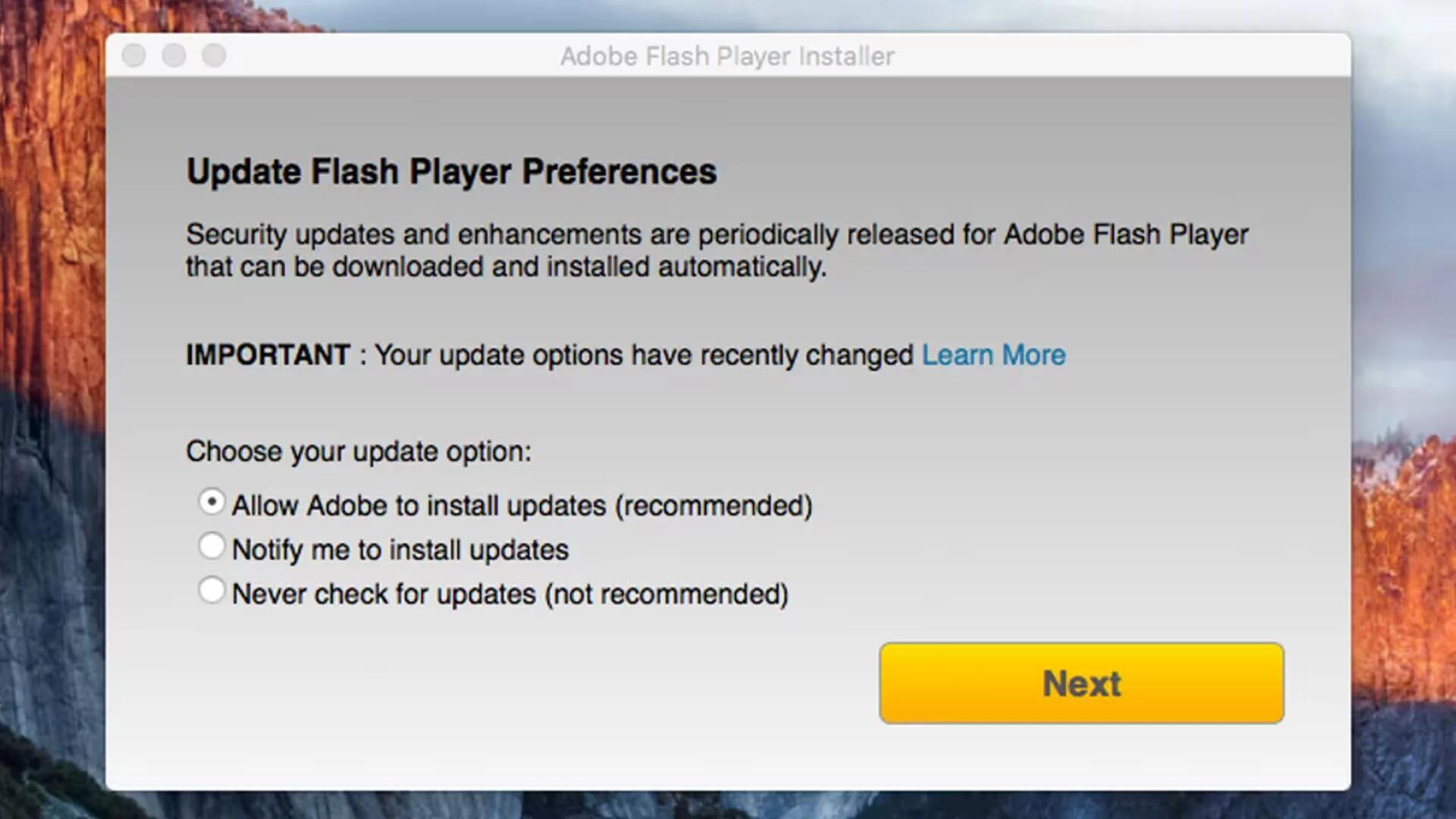
Windows Malware “Snake” Comes To macOS By Imitating Adobe Flash Player Installer
A new piece of backdoor malware called Snake that was originally found on Windows has been ported to the Mac for the first time.


