Apple Responds to Masque Attack Vulnerability, Says It Is Unaware Of Any Affected Users
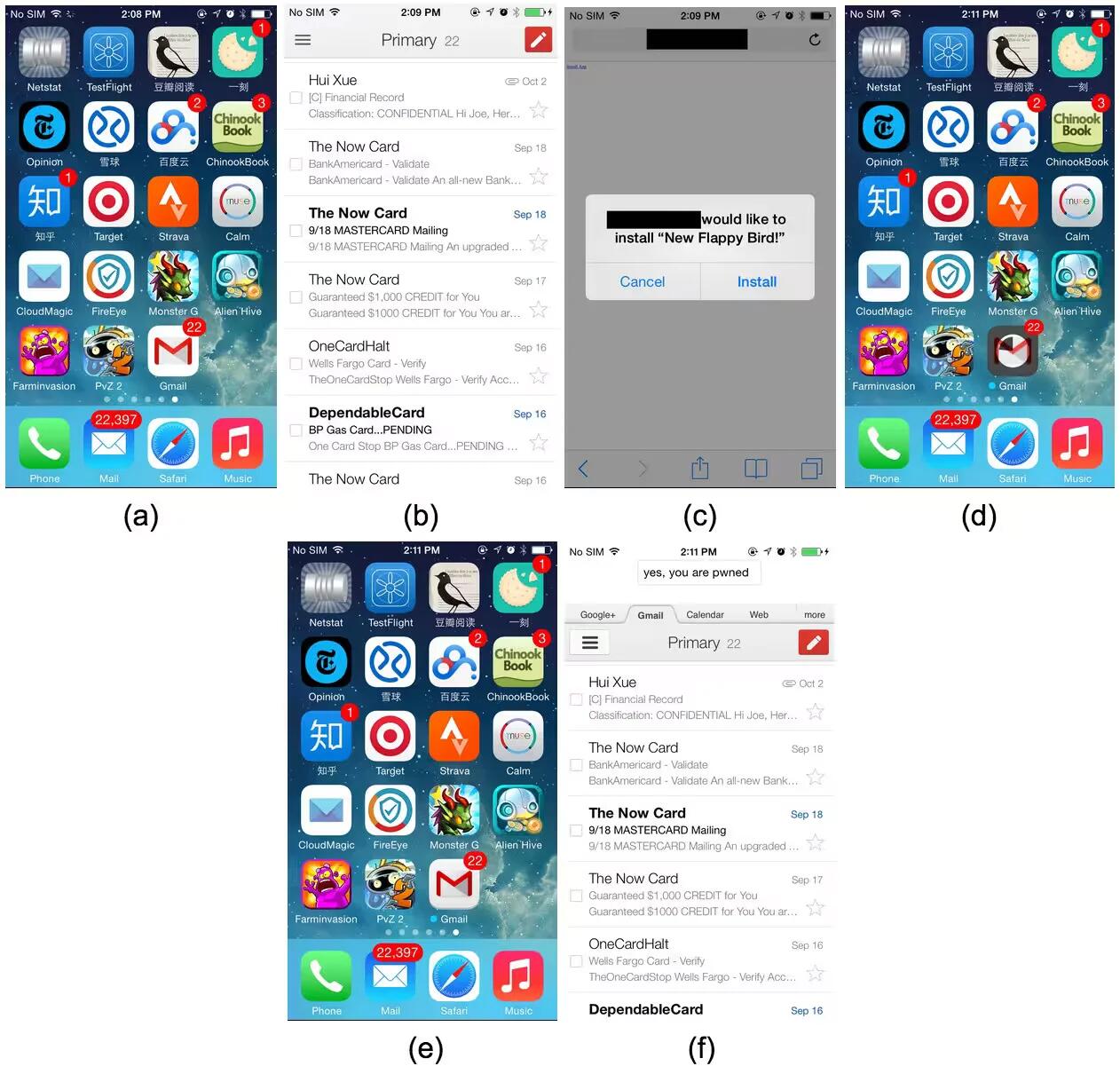
Just after couple of days after the discovery of an iOS vulnerability referred to as “Masque Attack”, that allowed malicious applications to be installed in place of valid apps and access user data, Apple hasissued a response to iMore.
We designed OS X and iOS with built-in security safeguards to help protect customers and warn them before installing potentially malicious software… We’re not aware of any customers that have actually been affected by this attack. We encourage customers to only download from trusted sources like the App Store and to pay attention to any warnings as they download apps. Enterprise users installing custom apps should install apps from their company’s secure website.
Masque Attack works by luring a user to install an app outside of the iOS App Store by clicking a phishing link in a text message or email or from a malicious website. For example, a user could be prompted to download a new app in a text message that says something like “Hey, try out Flappy Bird 2”. A user is then directed to a website where they’re prompted to download the app, which will install the fake app over the legitimate one using iOS enterprise provision profiles, making it virtually undetectable.
Earlier today the Department of Homeland Security issued a warning about the potential security issues it poses. The vulnerability was discovered just a week after reports of malware called WireLurker surfaced. WireLurker is able to attack iOS devices through OS X using a USB cable.
Both WireLurker and Masque Attack can be avoided by staying away from suspicious apps and avoiding links that prompt users to install apps outside of Apple’s App Stores.